Researchers of the Qihoo 360 Helping Hurricanes today filled in on two of the two solar-powered training programs found in the wild, designed for off-the-grid network equipment created by Taiwanese DrayTek.
According to the report, two separate groups of hackers used two major vulnerabilities related to the implementation of remote commands (CVE-2020-8515), related to business changes, DrayTek Vigor VPN account load, access and access points and listeners. settings are next.
Zero Day attacks that began in late November or early December are likely to continue with thousands of DrayTek people, Vigor 2960 3900, 300B unmanned devices. the new trader. The updates were released last month.
The non-everyday vulnerabilities mentioned can cause remote attackers who do not have the authority to send and execute breach orders on the system and have been described by a private researcher on his blog.
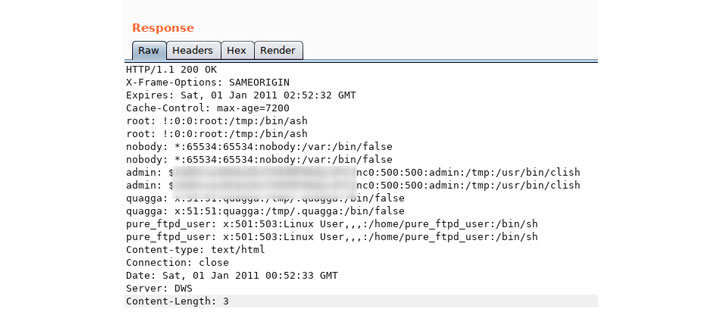
"The two 0-day deployment options include KeyPath and rtick located at /www/cgi-bin/mainfunction.cgi, and the downstream web interface is / usr / sbin / lighttpd," i the report said.
NetLab researchers have not yet launched two attacks against one group, but confirmed that, while the first group only explored on the network, the second group of malicious users used vulnerabilities to implement the rtick commands to create:
the backlash of the late website event
SSH backdoor on TCP ports 22335 and 32459,
backdoor system with user account w and password caonimuqin.
It should be noted that if you have installed the firmware or are currently installing it, you will not be able to remove all the backups until they have passed.
"We recommend that DrayTek Vigor users check and update their time, and check for their tcpdump protocol, SSH backdoor account, website backdoor, etc."
"If you have a problem with your router, turn it off if you don't want it and use the access control list whenever possible," the company says.
List of broken firmware components:
Vigor2960 <v1.5.1
Vigor300B <v1.5.1
Vigor3900 <v1.5.1
VigorSwitch20P2121 <= v2.3.2
VigorSwitch20G1280 <= v2.3.2
VigorSwitch20P1280 <= v2.3.2
VigorSwitch20G2280 <= v2.3.2
VigorSwitch20P2280 <= v2.3.2
Interested companies and citizens are encouraged to introduce new firmware updates to protect their valuable networks from malware and new cyber threats.

According to the report, two separate groups of hackers used two major vulnerabilities related to the implementation of remote commands (CVE-2020-8515), related to business changes, DrayTek Vigor VPN account load, access and access points and listeners. settings are next.
Zero Day attacks that began in late November or early December are likely to continue with thousands of DrayTek people, Vigor 2960 3900, 300B unmanned devices. the new trader. The updates were released last month.
The non-everyday vulnerabilities mentioned can cause remote attackers who do not have the authority to send and execute breach orders on the system and have been described by a private researcher on his blog.

"The two 0-day deployment options include KeyPath and rtick located at /www/cgi-bin/mainfunction.cgi, and the downstream web interface is / usr / sbin / lighttpd," i the report said.
NetLab researchers have not yet launched two attacks against one group, but confirmed that, while the first group only explored on the network, the second group of malicious users used vulnerabilities to implement the rtick commands to create:
the backlash of the late website event
SSH backdoor on TCP ports 22335 and 32459,
backdoor system with user account w and password caonimuqin.
It should be noted that if you have installed the firmware or are currently installing it, you will not be able to remove all the backups until they have passed.
"We recommend that DrayTek Vigor users check and update their time, and check for their tcpdump protocol, SSH backdoor account, website backdoor, etc."
"If you have a problem with your router, turn it off if you don't want it and use the access control list whenever possible," the company says.
List of broken firmware components:
Vigor2960 <v1.5.1
Vigor300B <v1.5.1
Vigor3900 <v1.5.1
VigorSwitch20P2121 <= v2.3.2
VigorSwitch20G1280 <= v2.3.2
VigorSwitch20P1280 <= v2.3.2
VigorSwitch20G2280 <= v2.3.2
VigorSwitch20P2280 <= v2.3.2
Interested companies and citizens are encouraged to introduce new firmware updates to protect their valuable networks from malware and new cyber threats.





